How to prevent Telephony Denial of Service (TDoS) attacks
Telephony Denial of Service (TDoS) attacks can overwhelm critical telephone systems, such as emergency response numbers or call centers. The good news: effective solutions are available.
TDoS attack profiles
There are different versions of TDoS attacks. They share a common feature in generating many calls to a destination, which eventually overwhelms the PBx or trunk. They vary in how these calls are generated.
Centralized TDoS attack
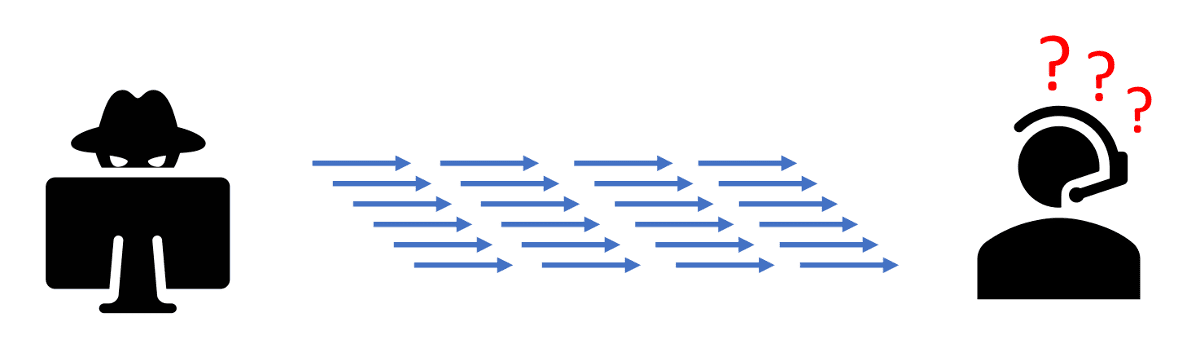
In a centralized TDoS attack, computer software is used to generate many calls from one source.
Distributed TDoS attack
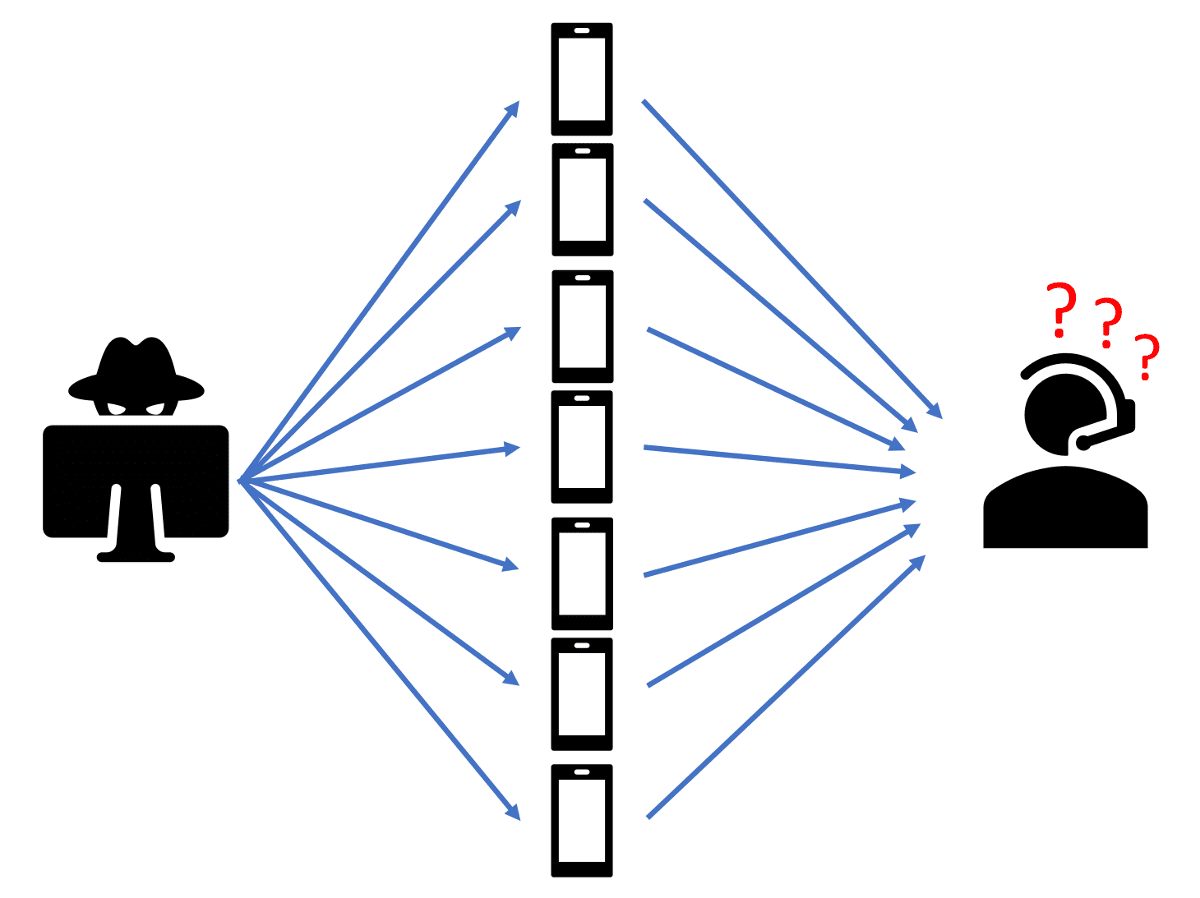
With a distributed TDoS attack, malware is distributed to many call sources to programmatically generate lots of calls at the same time.

Both centralized and distributed attacks are intended to shut down telephone service. Why would anyone want to do that? Here are a few motives that law enforcement officials have identified:
- Pranks by hackers—just to see if they can do it
- In 2016, an 18-year-old in Arizona launched a distributed TDoS attack that took down 911 service in 12 states
- Divert attention while hacking another system
- Prevent calls to financial institutions while making fraudulent charges
- Disable 911 emergency response during a terrorist attack
Oddly enough, TDoS can also be unintentional. Robocall perpetrators sometimes code their autodialer to rapidly scroll through blocks of numbers. The actually hope that people will answer their calls.
But if their autodialer script hits a block of numbers assigned to a hospital, for example, it could tie up all of the phone lines and staff answering the calls, crippling the delivery of critical services.
TDoS prevention
The first defense against TDoS is to use the Trusted IP Address feature in your peering SBC to prevent it from attempting to respond to messages from untrusted IP addresses. This can help defend against TDoS attacks that send packets to your SBC from outside of your established network connections.
With any of these robocall scenarios, attacks can be further mitigated by analyzing call traffic. When the volume of traffic breaches a threshold, further calls are blocked or diverted, ending the attack.
In a centralized attack or robocall pattern, the fraud prevention software scores telephone calls with common attributes, such as calling and called numbers, users and groups. When the cumulative score for a commmon grouping breaches a threshold, further calls are blocked or diverted to IVR for a period of time. The attack is ended.
With a distributed attack, fraud prevention software scores call traffic to a destination. When the cumulative score of calls to a given number crosses a threshold, further calls to that destination are diverted to an Interactive Voice Response (IVR) system for screening. The IVR prompts the caller for a response, which the distributed malware cannot provide. The attack is over.
TransNexus TDoS prevention solutions
We offer services with our NexOSS and ClearIP software products to prevent TDoS attacks:
- SIP Analytics analyzes call traffic for detection of TDoS attacks, fraud attacks and unwanted robocalls. Once detected, calls can be blocked or diverted.
- CAPTCHA gateway is an IVR system that accepts diverted calls and prompts for human interaction.
We offer these services on-premises or in the cloud, providing scalability to defeat any TDoS attack.
Contact us today for more information on TDoS prevention.
More on TransNexus.com
February 15, 2023
Suggestions to curb access arbitrage
June 27, 2022
FCC proposes new rules to prevent access stimulation
June 6, 2022
Denial of service attack and ransom demand defeated
May 18, 2022
China cracks down on telecom fraud
December 6, 2021
Telecom fraud losses increasing, according to CFCA report
December 1, 2020
FCC Report and Order on one-ring scam calls
November 9, 2020
Domestic telecom toll fraud is still a problem
October 12, 2020
FCC changes rules for intercarrier compensation on toll free calls
January 23, 2020
TRACED Act calls for one-ring scam protection
November 19, 2019
Robocall and TDoS case studies
October 28, 2019
FCC denies stay request on their Access Arbitrage Order
October 28, 2019
Wangiri telecom fraud activity reported in Canada
September 26, 2019
FCC issues order to prevent access stimulation
July 16, 2019
ClearIP adds new call forwarding blacklist capabilities
July 10, 2019
July holiday week telecom fraud attack profiles
June 13, 2019
ClearIP enhancements for blacklisting of SPID and location
May 20, 2019
Anatomy of a telecom fraud attack
May 14, 2019
Study on rule changes to eliminate access arbitrage
May 8, 2019
FCC warns of Wangiri telecom fraud scams
March 8, 2019
SIP Analytics vs. CDR-based fraud management – a case study
October 22, 2018
FCC proposal to curb domestic telecom fraud
September 27, 2018
SIP Analytics® inspects each call before it begins. It’s the fastest, most precise method available to detect and prevent telecom toll fraud.
Learn more