July holiday week telecom fraud attack profiles
We noticed a spike in attempted telecom fraud attacks in the U.S. during the Fourth of July holiday week. Here’s an overview of the attack profiles. The more you know about telecom fraud attacks, the better you can keep your network and subscribers safe.
In this post, we’ll share information about attack profiles by destination type and by day. Then we’ll take a closer look at a domestic fraud attack.
Telecom fraud attacks by destination type
We categorized each attack by the following destination types:
- Domestic. Calls attempted to high cost destinations within the U.S., for example, access stimulation destinations in Iowa and South Dakota.
- Caribbean. Calls attempted to high cost numbers among Caribbean countries within the North American Numbering Plan, for example, Jamaica, the Dominican Republic and others.
- IRSF (International Revenue Sharing Fraud). Calls to other high cost destinations around the world.
The following charts measure telecom fraud attacks encountered by several carriers during July 1–7. Each attack included several call attempts.
Fraud attacks by destination type
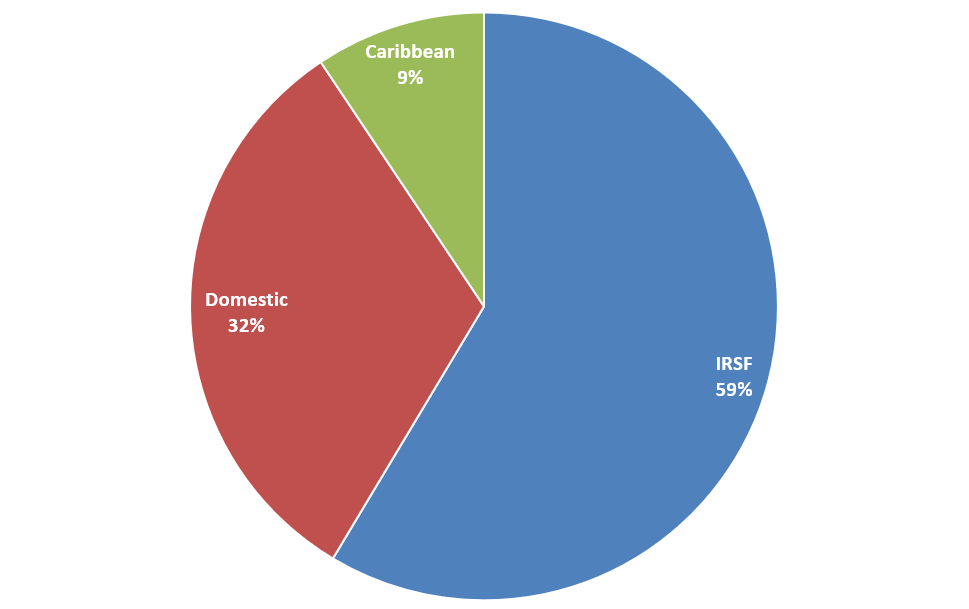
Most attack destinations were IRSF, as you might expect. These calls have the highest cost destinations.
However, over 41% of these telecom fraud attacks were destined for Domestic and Caribbean numbers. This result reinforces a trend we’ve been noticing for a while: as more carriers focus their efforts on preventing IRSF, fraudsters are turning their efforts to high cost Domestic and Caribbean destinations. The potential payoff isn’t as big, but some carriers aren’t monitoring this traffic as closely for telecom fraud attacks.
Telecom fraud attacks by day, by destination type
This result might surprise you: one might expect that telecom fraud attacks would spike on the July 4 holiday, when victims might be less apt to notice. However, fraudsters sent most fraud attacks the day before, on July 3.
Holiday week fraud attacks by day by type
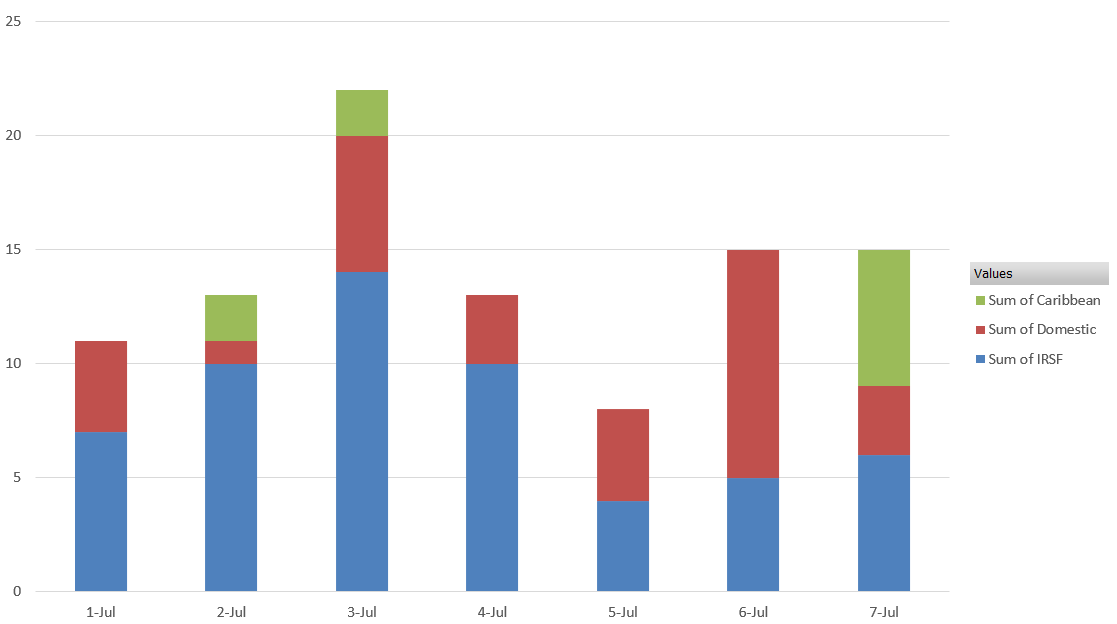
Why did fraudsters do this? We really don’t know. Perhaps they figure their victims would be anxious to get away for the holiday and wouldn’t be paying close attention.
Notice too how the mix of destination types changed over the holiday week. IRSF attacks spiked on Wednesday, the day before the holiday. Domestic attacks spiked on Saturday, while Caribbean attacks spiked on Sunday.
Attack response
These telecom fraud attacks were detected and blocked by SIP Analytics®. Here’s a chart that shows how SIP Analytics responded to one of the attacks:
SIP Analytics attack response
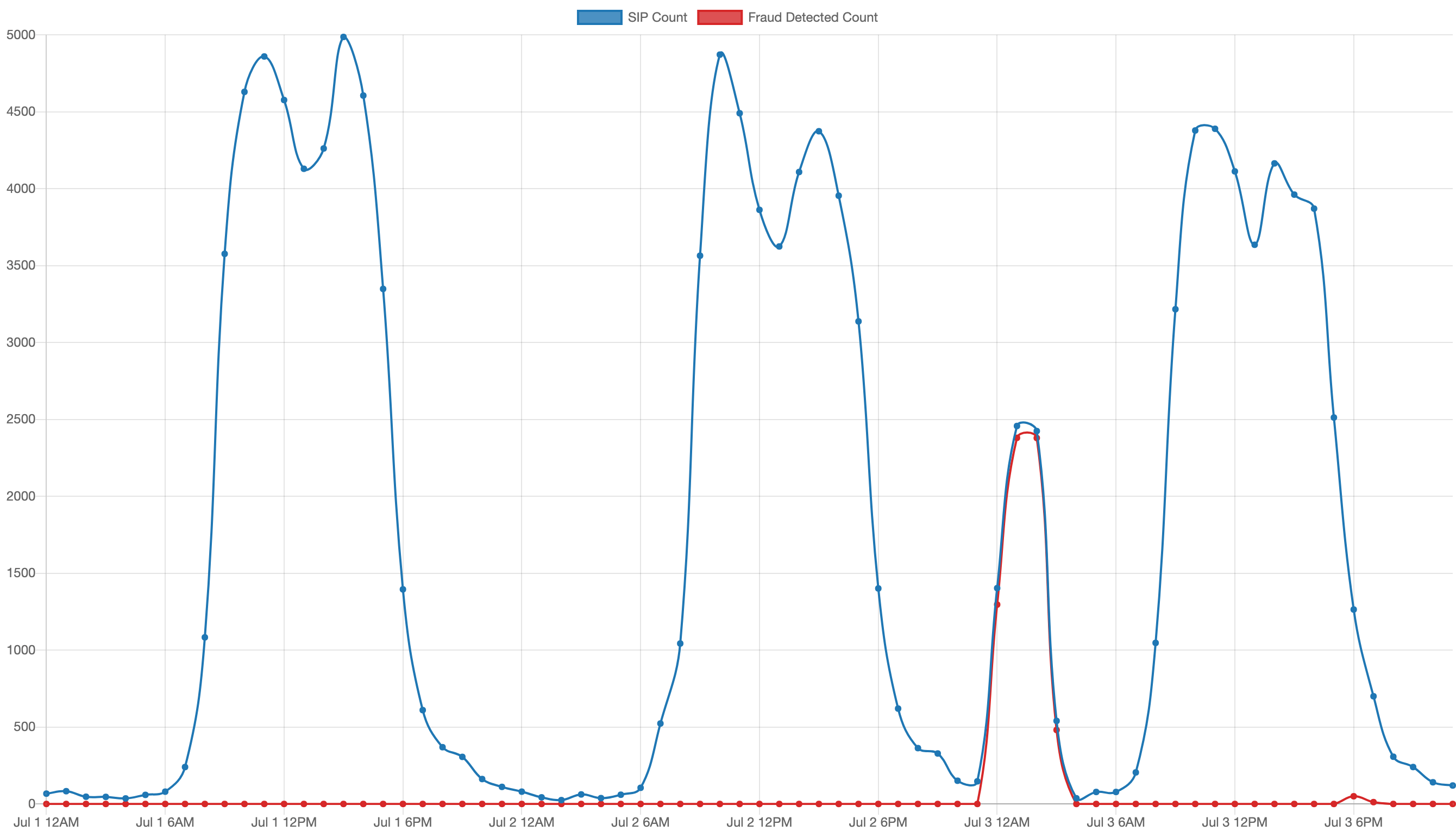
The chart shows call activity from July 1–3. The blue line is normal call activity over these three days, and the red line shows calls blocked in response to a telecom fraud attack in the middle of the night between the second and third day.
There’s almost no gap between the red and blue lines during this fraud event, which shows how quickly SIP Analytics shut down the attack.
This was a high-call-volume domestic telecom fraud attack targeting a range of numbers in area code 605 in South Dakota. All calls had the following attributes:
| Called SPID/OCN: | 870F |
| Called Rate Center: | PINE RIDGE |
| Called LATA: | 640 |
| Called Company Name: | NATIVE AMERICAN TELECOM - PINE |
SIP Analytics blocked over 6,500 call attempts made by this attack, with no service disruption of normal calls.
TransNexus telecom fraud prevention software
SIP Analytics quickly protected these service providers and their subscribers. These telecom fraud attacks were unsuccessful.
SIP Analytics response time will vary based upon the nature of the telecom fraud attack. It uses machine learning, statistical analytics and sensitivity controls to compare call activity with known threat profiles and block fraudulent calls. See our whitepaper, Block telecom fraud faster, for more information.
SIP Analytics is available in our ClearIP and NexOSS software products. Contact us today to learn how we can protect your network and subscribers from telecom fraud attacks using SIP Analytics.
