Robocall mitigation
Robocall mitigation refers to processes that make illegal robocalls less severe, dangerous, or damaging. In the U.S., the phrase has acquired a specific legal and regulatory meaning: Robocall mitigation describes programs used by voice service providers to prevent unlawful robocalls from originating on their network.
The TRACED Act and subsequent FCC orders require voice service providers to use STIR/SHAKEN call authentication and a Robocall Mitigation Program on every call they originate.
All providers must file a Robocall Mitigation Certification with the FCC.
Calls with U.S. NANP calling numbers from any provider not registered with the FCC Robocall Mitigation Database must be blocked.
These requirements fall on every provider. To summarize, you must:
- Use STIR/SHAKEN or a Robocall Mitigation Program on every call you originate with U.S. NANP calling numbers,
- File a Robocall Mitigation Certification with the FCC,
- Block calls with U.S. NANP calling numbers from providers that don’t have a Robocall Mitigation Certification on file.
If you do not certify, then other service providers are required to block your calls.

Mitigation versus Prevention
Voice service providers and most consumers are familiar with robocall prevention measures to block suspected robocalls at termination. Robocall prevention provides relief to subscribers who are tired of getting nuisance robocalls.
The TRACED Act and subsequent FCC orders require robocall mitigation to prevent robocalls at origination.
- Robocall prevention: Reduce or eliminate incoming illegal robocalls while terminating calls to your subscribers.
- Robocall mitigation: Reduce or eliminate outbound illegal robocalls originating on your network. The TRACED Act and FCC orders mandate robocall mitigation for calls originating with U.S. NANP numbers.
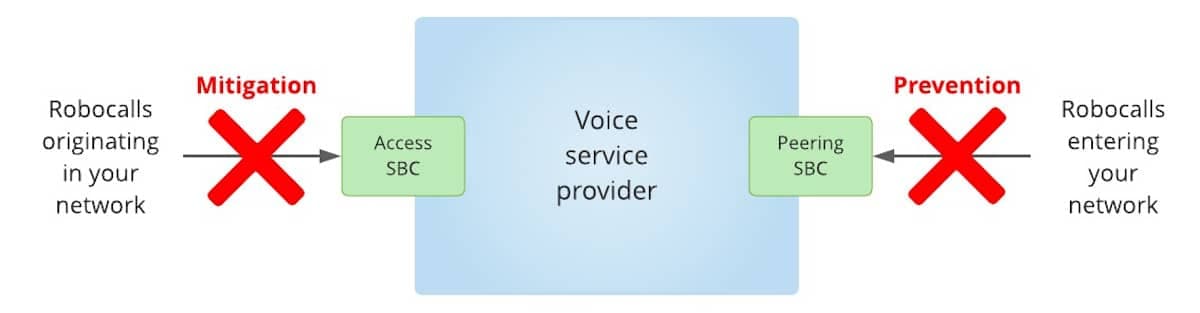
Robocall Mitigation and Prevention
Some robocall prevention measures are applications that end users install on their smartphones. These apps can identify and block or divert incoming robocalls. Originating service providers cannot rely on such apps for robocall mitigation.
Robocall mitigation methods
Here are robocall mitigation methods that have proven highly effective in identifying and blocking robocalls. These methods can be applied to calls at origination or termination. They can “reasonably be expected to significantly reduce the origination of illegal robocalls” as required by the FCC.
TransNexus can help you identify and deploy the methods that would be most appropriate for your circumstances. We can also help you fast-track your Robocall Mitigation Certification filing based on the methods that you choose.
Blacklists
You can use blacklists to mitigate robocalls with specific attributes, including:
- Calling telephone numbers or prefixes
- Calling SPIDs (OCNs) that are not yours
- Calling locations, e.g., states/provinces/regions that are not yours
- Calling countries that are not yours
- IP addresses that you have identified as robocallers
- User agents that your customers do not use, but robocallers do use.
When a call is identified by a blacklisted attribute, you can either block the call or divert it to a CAPTCHA gateway for Interactive-Voice-Response screening. You can review blacklisted call origination reports to investigate the underlying causes.

Shield

You can use Shield for robocall mitigation to screen calls at origination for calling numbers that are invalid, high-risk, or appear on Do Not Originate lists.
You can set policies by groups, subscribers, and numbers to control the handling of such calls. For example, these calls can be blocked, diverted, or reported.
Reputation
You can perform a reputation lookup on calling numbers at origination for robocall mitigation. This lookup returns a reputation score from 0 to 100. The higher the number, the worse the reputation.
If your customer has a calling number with a poor reputation, you may find that they are a victim of number spoofing. We can help you repair the reputation of their number with reputation analytics companies, or you may wish to issue them a different number.

Dynamic traffic analysis
You can use real-time dynamic traffic analysis, called SIP Analytics, to detect and mitigate robocalls at origination. SIP Analytics monitors all originated calls by source over a rolling 60-minute window. It compares cumulative call count by source within this window with thresholds that trigger a response to a robocalling event.
SIP Analytics is self-learning. Thresholds are based on call history and are updated dynamically in real time. A legitimate high-volume caller would therefore acquire a higher threshold, while a residential consumer would typically acquire a lower threshold. Default thresholds are used for a new source until it accumulates sufficient history to enable the calculation of dynamic thresholds.
When a cumulative call count for a specific source breaches a threshold, calls from that source can either be blocked or diverted. In either case, you can investigate to determine whether the caller was originating unlawful robocalls.
CAPTCHA
The CAPTCHA gateway can be used in conjunction with the robocall mitigation methods listed above. When a method triggers an action, the CAPTCHA can be invoked to determine whether the caller is a human or an autodialer.
The CAPTCHA prompts the caller for a random two-digit code. If a human is placing the call and they answer the prompt correctly, then the CAPTCHA gateway will allow the call to proceed. If the call is placed by an autodialer, which cannot answer the prompt correctly, then the call can be blocked, diverted to voicemail, or reported.

Call Detail Record (CDR) analysis

You can collect CDRs from your network equipment and review them with NexOSS for robocall mitigation. You can develop reports to look for unexpected high call volume, short call duration, call hang-ups by called party, and so forth. If you find suspicious call activity, then you can investigate.
STIR/SHAKEN
The TRACED Act and subsequent FCC orders mandate both robocall mitigation and STIR/SHAKEN call authentication.
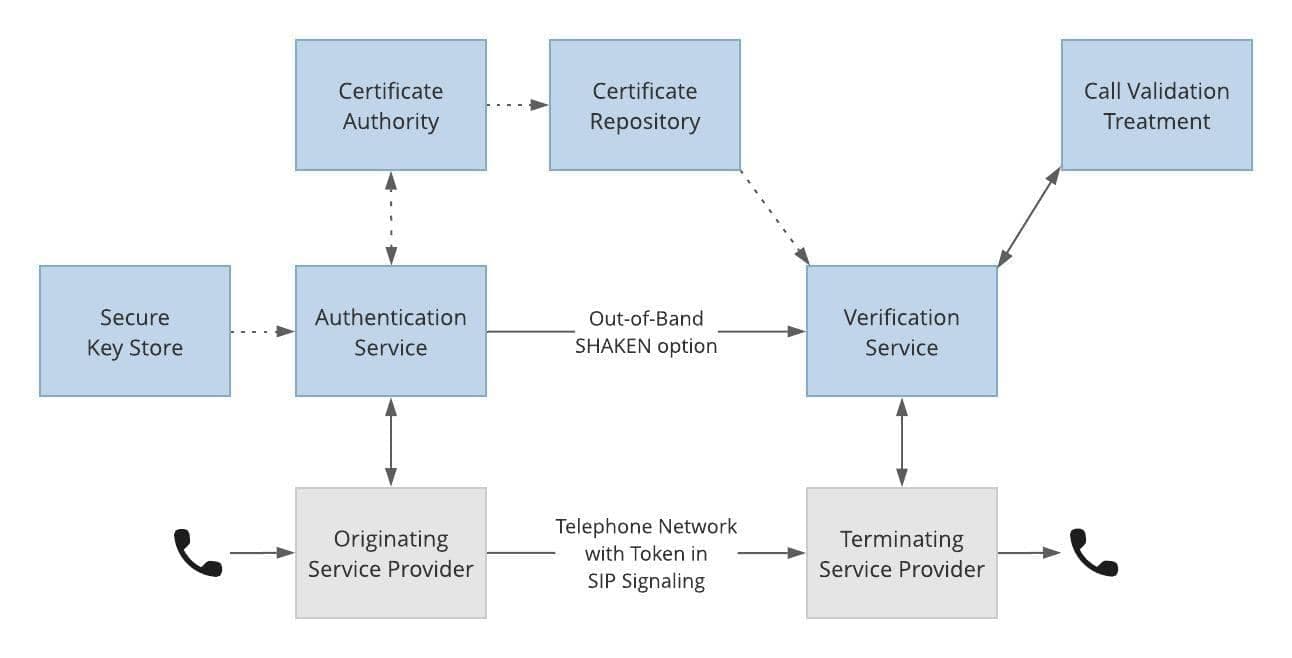
TransNexus STIR/SHAKEN Solutions Provide Everything You Need
We provide comprehensive STIR/SHAKEN solutions with our ClearIP and NexOSS software platforms—the same platforms that provide the robocall mitigation solutions listed above.
This gives you an important benefit: using one software platform for both robocall mitigation and STIR/SHAKEN makes deployment easy.
TransNexus robocall mitigation solutions
We offer robocall mitigation solutions in our ClearIP and NexOSS software products. We can help you deploy them quickly and easily.
In addition, we can help you plan, prepare, and complete your Robocall Mitigation Certification filing. Your filing will demonstrate to the Commission that your voice service business has deployed effective robocall mitigation measures in production.
Contact us today to learn how we can help you tailor a robocall mitigation program to your circumstances and satisfy compliance requirements.
Our STIR/SHAKEN products:
- Work with your existing network
- Support SIP and TDM
- Affordable, easy to deploy